WS-Security SAML Token |
|
WS-Security is a standard for securing Web services. This standard provides various ways of authentication and credential formats. The SAML token profile can be used when there is a need to work with other authentication or authorization systems. As integrity of message is important, you should use message-level or transport-level (example SSL) security. SAML and WS-Security are emerging standards and are used in many large enterprise systems.
The WS-Security SAML token contains credentials in the form of assertions. These SAML assertions are proof that a user correctly authenticated with Single Sign-On. The client verifies the user credentials with Single Sign-On before a Web service is used. Single Sign-On returns assertions after verifying the credentials. The following diagram describes this process.
The client requests SAML assertions by Single Sign-On
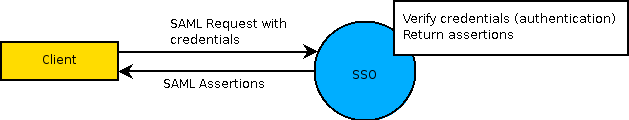
The client then includes these assertions in the request header to the service container. The service container reads the assertions and checks if the user is authorized to complete the request. The request is executed only after ensuring that the user is authorized to work with the service container. The following diagram describes the request to the service container.
The client includes SAML assertions in each SOAP request
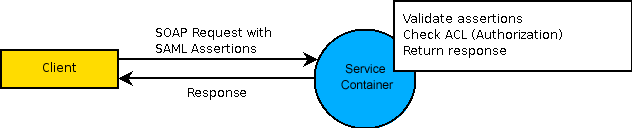
The SAML assertions can by provided by Single Sign-On, or by any other identity provider that supports the SAML standard. The credentials supplied to Single Sign-On can consist of all the identity types that Process Platform supports.
If the SAML assertions are signed, the service container must trust the signing certificate and the entire chain of certificates of Single Sign-On that provided the assertions. Trust relations can be set in Security Administration.
The SOAP request will be executed only if the following conditions are met:
- The assertions are valid, well-formed, and are not expired.
- The service container that received the request trusts Single Sign-On which provided the SAML assertions (if signing is mandatory for the service container).
- The SAML assertions can be mapped to a valid Cordys user.
- The user has authorization to execute the SOAP request.
Configuration
- The Web server must be configured explicitly to allow anonymous access. When this is configured, the Web server will not try to authenticate, but the client must provide valid credentials in the SOAP message.
- An authenticator must be configured in the service group configuration in LDAP and this authenticator is used for verifying the credentials.
Example
For an example of WS-Security SAML token, refer to Example of SAML Token.